kd❯ g
fffff803'00000000 EB FE jmp short loc_HackinG
~ Linux Exploit Tips
Create Skeleton Exploit
- $ skel binary (private script)
- $ ropper --file binary --console
- $ (pivot/ELF/x86_64)> stack_pivot
- $ ropper --file binary
- $ ropper --file binary --search "pop rdi"
- $ ROPgadget --binary binary
- $ ROPgadget --binary binary --only "pop|ret"
- $ ROPgadget --binary binary >> gadgets.txt
- $ ./woollymammoth.py offset -t 127.0.0.1 -p 8080 --prefix "HELP "
- $ ./woollymammoth.py eip -e 33634132
- $ pattern 100 (private script)
- pwndbg> r (Cntl+C)
- pwndbg> search /bin/cat
- $ strings binary
- $ strings -tx libc.so | grep /bin/sh
- $ rabin2 -z binary
- $ objdump -s libc.so | less
- Use Pwntools
- pwndbg> vmmap
- $ objdump -h binary (.data and .bss used for write data)
- $ ldd binary
- $ afl
- $ rabin2 -i binary
- $ readelf -s binary
- $ readelf -s libc-2.19.so | grep system@
- Use Pwntools
- pwndbg> x/x $rbx (view hexa)
- pwndbg> x/10x $rbx (view 10 hexa)
- pwndbg> x/s $rbx (view string)
- pwndbg> x/10s $rbx (view 10 string)
- pwndbg> x/i $rbx (view assembly)
- pwndbg> x/10i $rbx (view 10 assembly)
- pwndbg> x/gx $rbx
- pwndbg> p/x $rbx (view pointer)
- pwndbg> plt
- pwndbg> got
- pwndbg> mmap
- pwndbg> vis
- pwndbg> b/break (Set breakpoint)
- pwndbg> disable (Disable breakpoint)
- pwndbg> del 1 (Delete breakpoint depending id)
- pwndbg> enable (Enable breakpoint)
- pwndbg> info breakpoints/ib (List breakpoints)
- pwndbg> watch (Break on access [read/write])
- pwndbg> r/run (Run program)
- pwndbg> s/si (Step over)
- pwndbg> n/ni (Step into)
- pwndbg> finish (Step to next return)
- pwndbg> u (Step to address)
- pwndbg> info registers (Show registers)
- pwndbg> info proc mappings (Show virtual memory map and permissions)
- pwndbg> print/p (Examine symbols)
- pwndbg> backtrace/bt (Stack backtrace)
- pwndbg> set follow-fork-mode parent
- pwndbg> set disassembly-flavor intel
- pwndbg> set follow-fork-mode child
- pwndbg> set detach-on-fork off
- pwndbg> info inferiors
- pwndbg> inferiors X
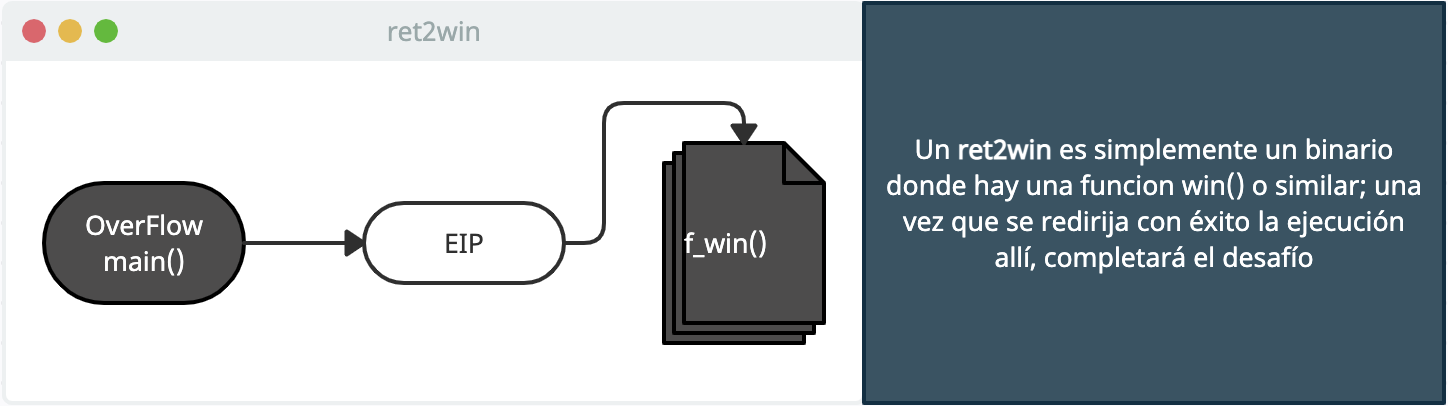
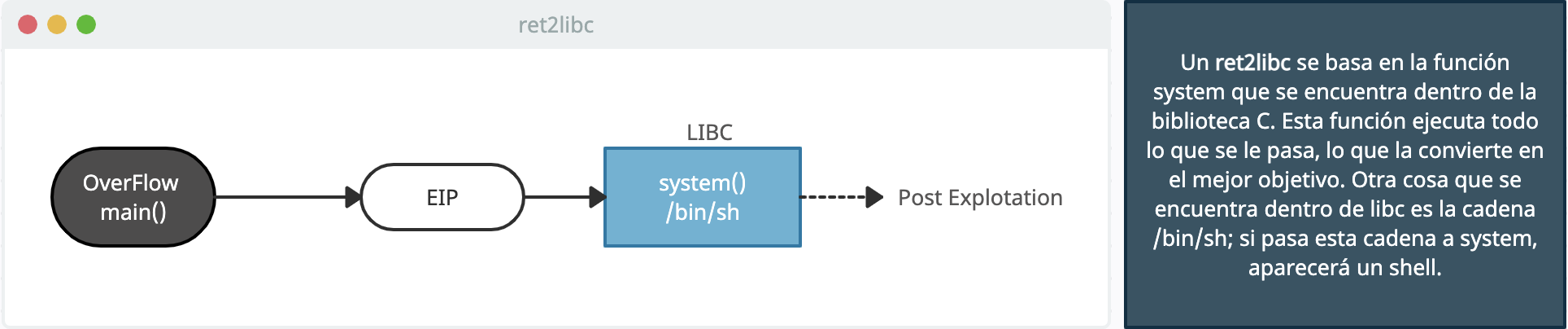
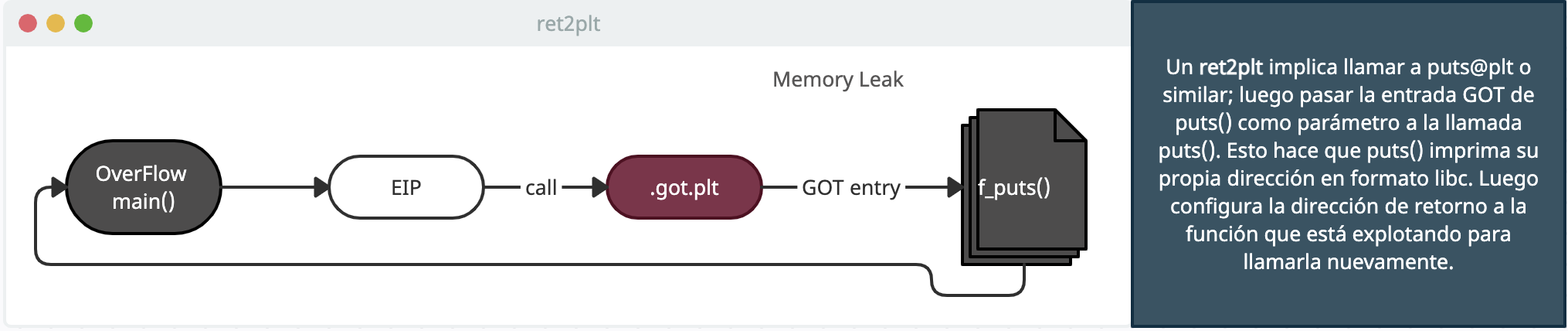
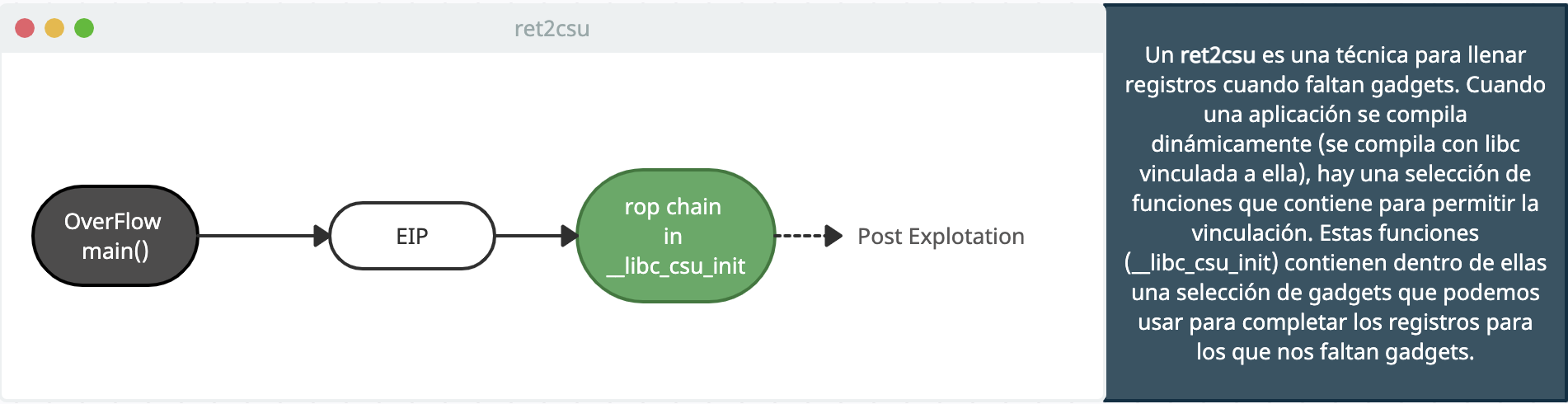
Links