kd❯ g
fffff803'00000000 EB FE jmp short loc_HackinG
~ ./priv
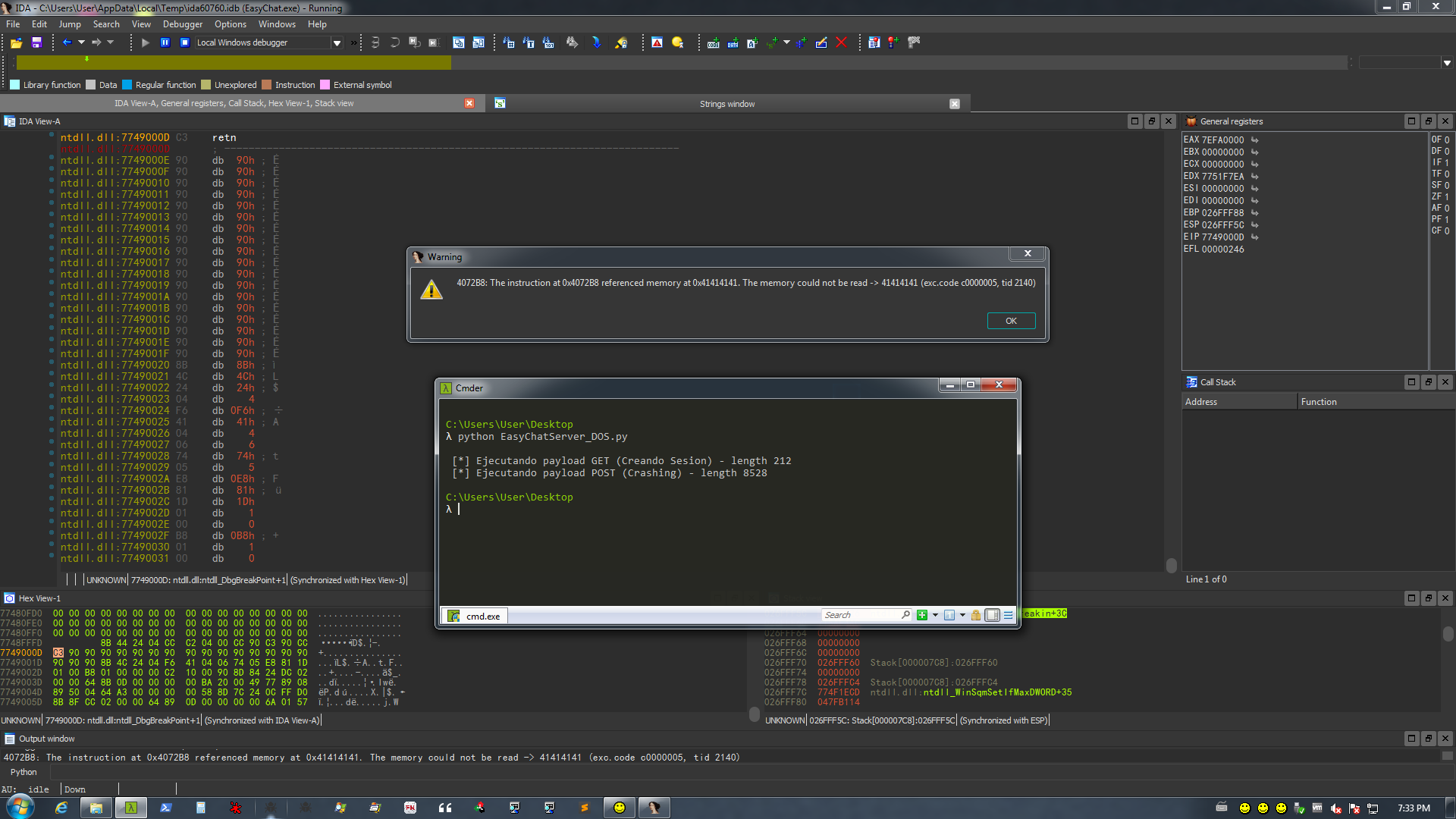
| EFS Easy Chat Server - CVE-2019-20502 |
|
|
|
body2.ghp receives a variable called message, which allows a buffer to overflow to produce an application block
|